Glory Tips About How To Kill Botnet

Botnets are an amplification attack:
How to kill botnet. Botnets are networks of hijacked computer devices used to carry out various scams and cyberattacks. These attacks are carried out by ‘brute force’ meaning they use excessive attempts to ‘force’ their way into your private accounts. See how they work and how to protect your devices and networks against them.
Although email is widely seen as an older vector for attack, spam botnets are some of the largest in size. How to prevent botnet attacks. If that doesn't work, you should try using a specialized botnet removal tool.
Network security what is botnet? A botnet is a collection of devices connected to the internet and controlled by hackers, often unbeknownst to the user. Make sure that any antivirus solution has full virus definitions that are updated daily to stay ahead of the malware game.
Over time, it has gotten more and more capable of advanced cybercrime. This is why you need to. A botnet can infect computers, laptops, servers, smartphones, and all kinds of iot devices with security vulnerabilities.
Here's how gcore can counter these threats. One of the persistent threats that organizations face is the use of botnets for malicious purposes. Experts believe that the development of serverless technologies will further simplify the creation of botnets for ddos attacks.
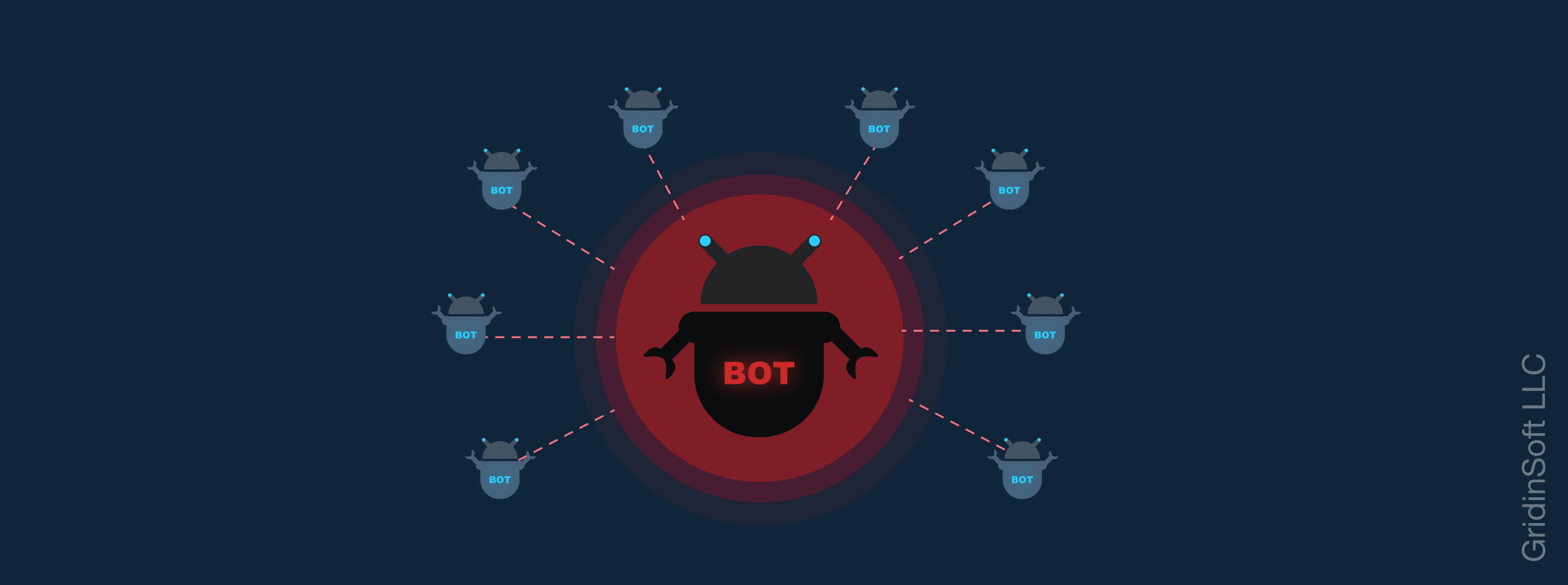
A botnet is a network of. Moobot was used to create a functional botnet of compromised routers that the gru and fancy bear were using for undisclosed reasons, but the scale of the security breach isn't promising. These crimes included vast spearphishing and.
First, try using a specialized malware removal tool. The term “botnet” is formed from the word’s “robot” and “network.”. A botnet attack can cover a wide range of malicious goals and setups.
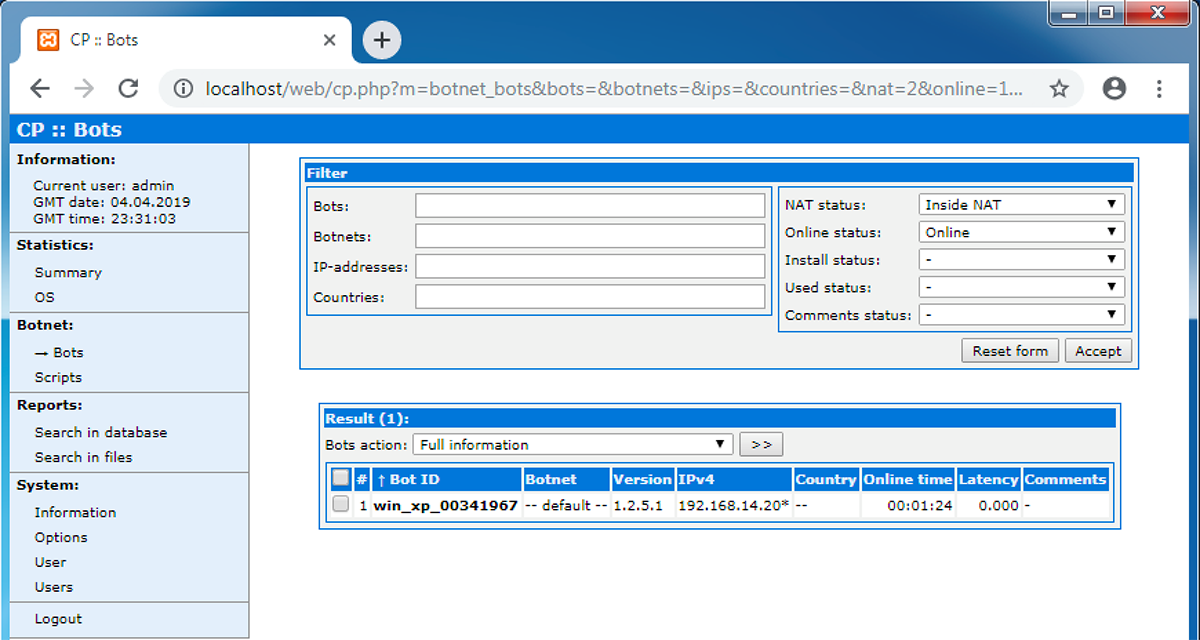
Some botnets include hundreds or even thousands of computers, making them one of the biggest online threats today. Chiradeep basumallick technical writer last updated: But that attack can effectively be any kind of cyberattack, meaning that if you want to prevent a bot attack you need to defend yourself against.
Install a windows firewall. Your firewall is your first layer of defense and the most basic cybersecurity tool you can use. Authorities believe the intelligence service used the botnet for malicious operations, including phishing attacks, credential harvesting, spying, and data theft against strategic targets and foreign governments.
Keep your systems and apps up to date. The bots serve as a tool to automate mass attacks, such as data. Why you should understand how botnets work as a security professional, understanding botnets is extremely important.